
Published January 27, 2020
Securing your Journey to the Cloud
Hugo Bishop, Senior Lead at Cisco Cloud Security UKI, shared his valuable insight into securing your journey to the cloud at the CISO Inspired conference.
Hugo believes that the key pillar of the shift to digital business transformation is business enablement: “It’s to deliver the best and most personalised experience for your customers and your employees; to transform your processes and your business models to be able to deliver that; and ultimately to empower your workforce and to enable them to maximise their potential and their efficiency.”
In the traditional IT model, all critical infrastructure, business applications and workstations were sat behind a firewall on the corporate network. Branch offices within the network were backhauled via MPLS and everything went out through the security controls on site. “That was great from a security perspective,” Hugo says. “But not so great from an agility perspective.” With more users needing to work remotely and access internet direct to cloud, organisations are now moving away from this traditional model and towards enablement.
“There are three iterations that we now see over the networks,” Hugo explains. “We see a predominantly on-premise, private DC approach – where there’s a little bit of connectivity, whether that’s on a mobile worker or a SaaS perspective – but most of the campuses still sit behind the enterprise edge. We see a Cloud First movement, where maybe 60 or 70% is now sitting in public cloud or SaaS, DIA or Direct to Cloud. And we see a Cloud All-In, or Cloud Native approach.”
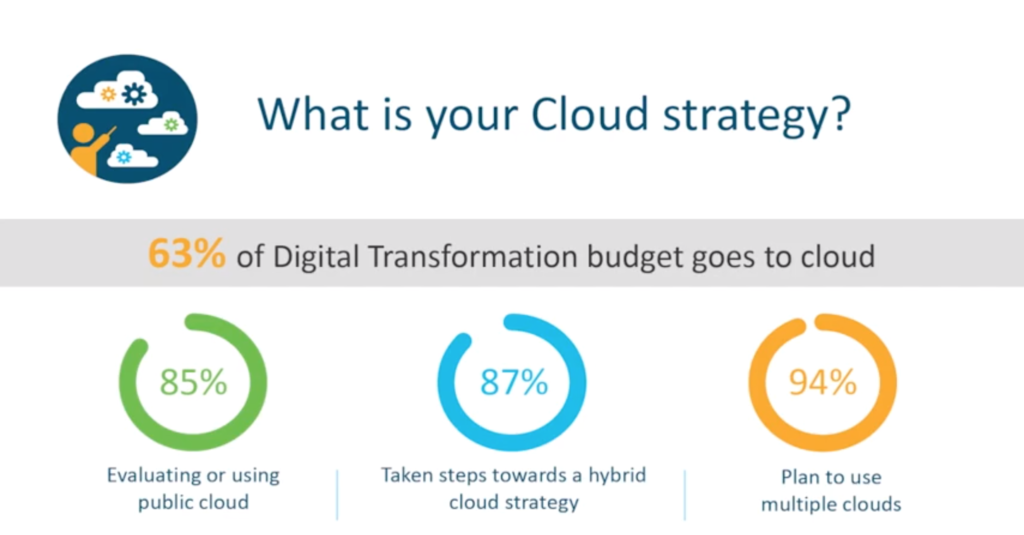
With 63% of digital transformation budget going to cloud, Hugo highlights how the way we work has changed: ” We see critical infrastructure now hosted in the cloud. We see a huge movement towards the mobile worker – which is brilliant from a business enablement perspective but brings challenges around security and visibility. We see critical business applications being hosted in the cloud. We’ve seen a big shift towards DIA in the branch – Cisco, in particular, is putting a lot of focus around the SD-WAN movement and how to secure that. But fundamentally, we are seeing a shift away from the traditional model to the more agile model and the challenges associated with that.
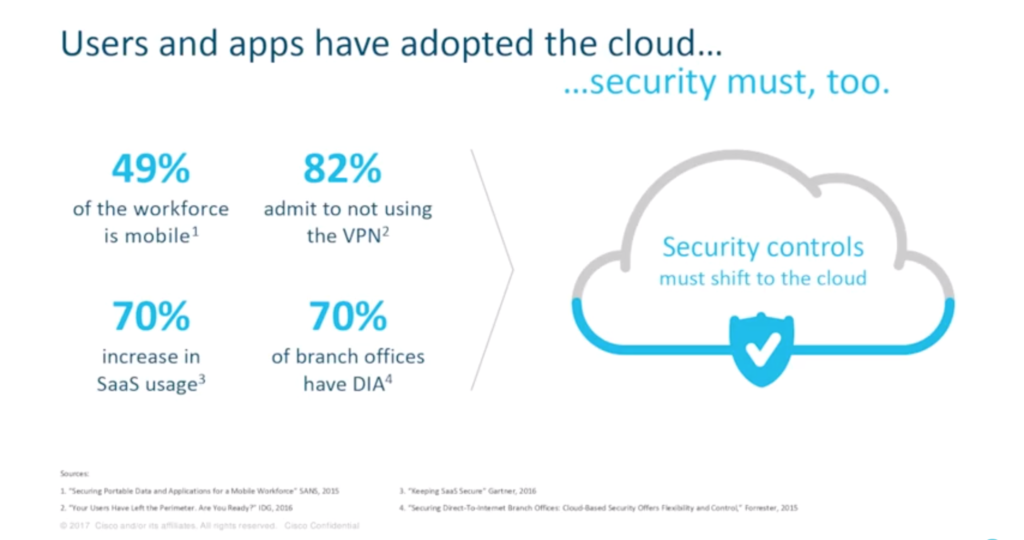
With users and apps adopting the cloud, it is important that security controls shift to the cloud too. Line of business executives and IT professionals must also work together to respond to digital disruption. “We’re seeing a lot of investment in the analytics side,” Hugo says. “Bringing that in-house and not having to rely on third parties or external bodies to deliver the analytics that you need to map across a significant spread of security toolsets and security risks.”
Cisco has noticed a trend of networking and security working more closely together, which Hugo believes is a necessity. “Looking at this in-house, we’ve got a drive behind the whole network intuitive model and using the network as an enabler,” he says. “But that’s very much hand-in-hand with security, and security underpins everything. We build security in from day one.”
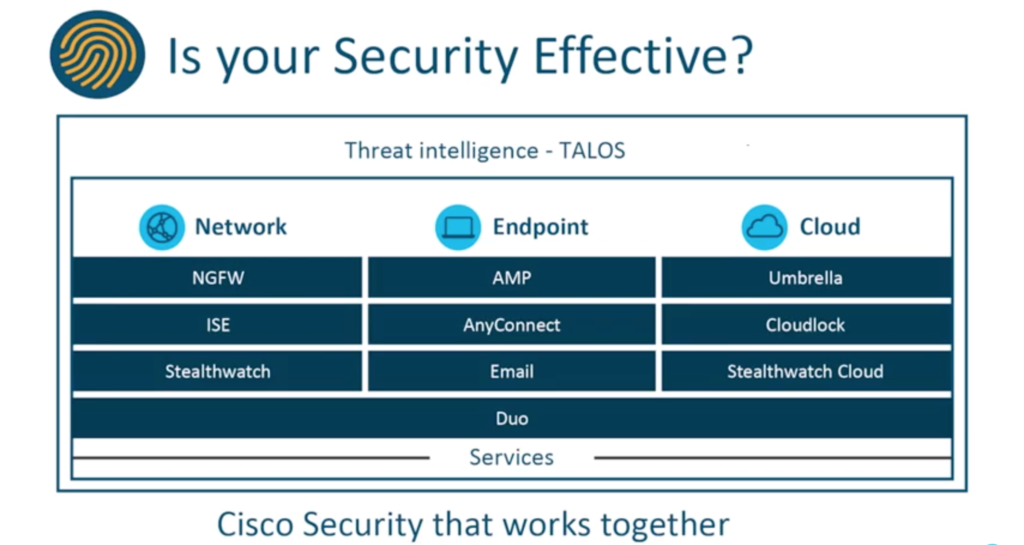
The Cisco security portfolio has three main areas: Network, Endpoint and Cloud. “Cisco’s development into security is predominantly around integrating these solutions, both at the back end and the front end,” Hugo explains. “Talos underpins everything from a security, research and analytics perspective.”
The key security challenges faced by Cisco customers include malware and ransomware; gaps in visibility, coverage and control; cloud apps and shadow IT; and difficult to manage security.
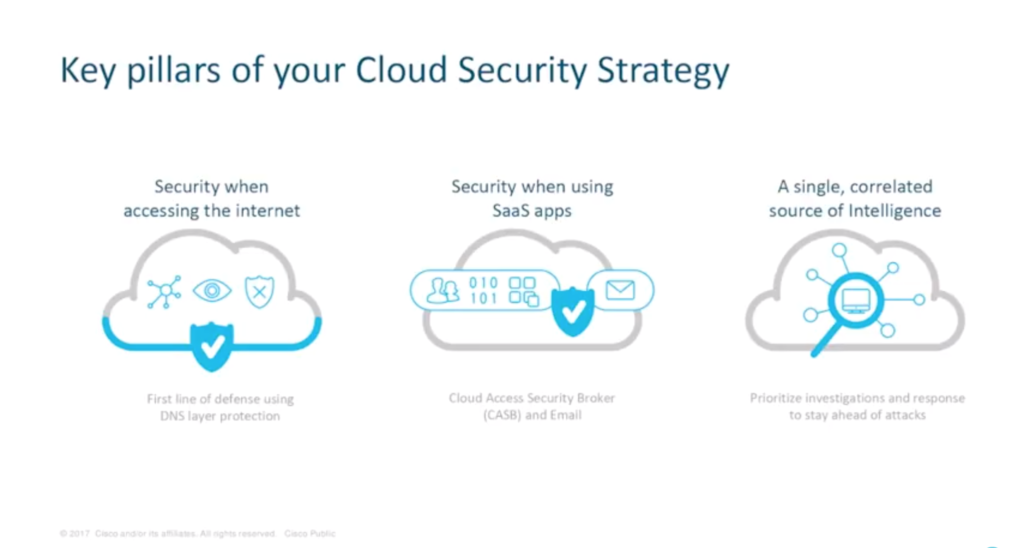
Hugo outlines the three key pillars of a cloud security strategy: secure access to the internet; security when using SaaS apps; and a single, correlated source of intelligence to prioritise investigations and speed up incident response times.
“Underpinning that, we see organisations investing in an adaptive MFA solution to easily enforce policies across networking applications,” he says. An adaptive MFA provides security when accessing any app, allowing organisations to easily enforce contextual policies based on security risks for each application.
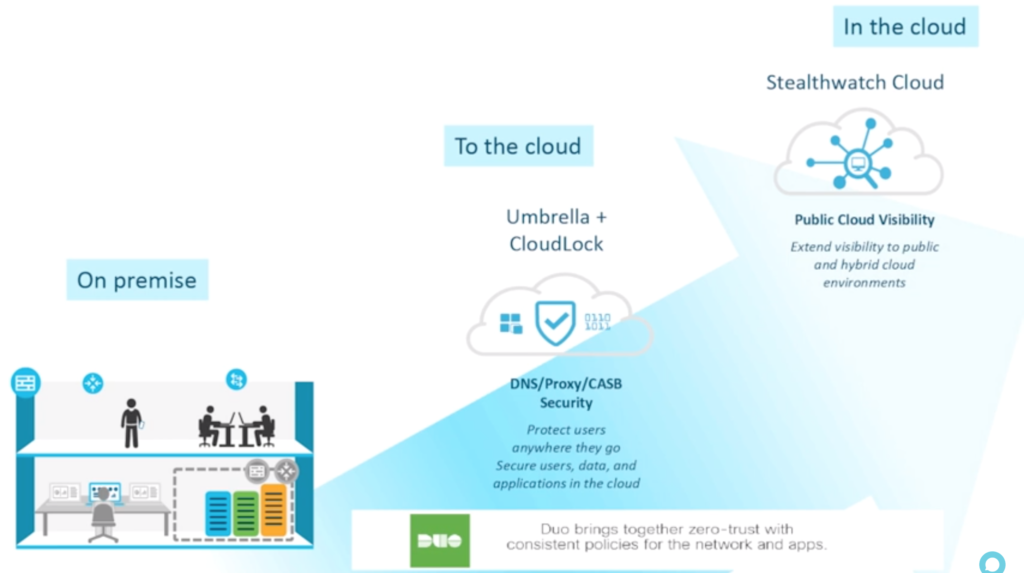
“On-premise security is obviously still critical,” Hugo says. “But as you move to the cloud, you’ve got solutions within the Cisco portfolio like Umbrella, which is our gateway service, and CloudLock, which is the CASB. Extending that visibility to the public and hybrid cloud environments, Cisco has a solution called Stealthwatch Cloud. And underpinning everything is Duo on the MFA.”
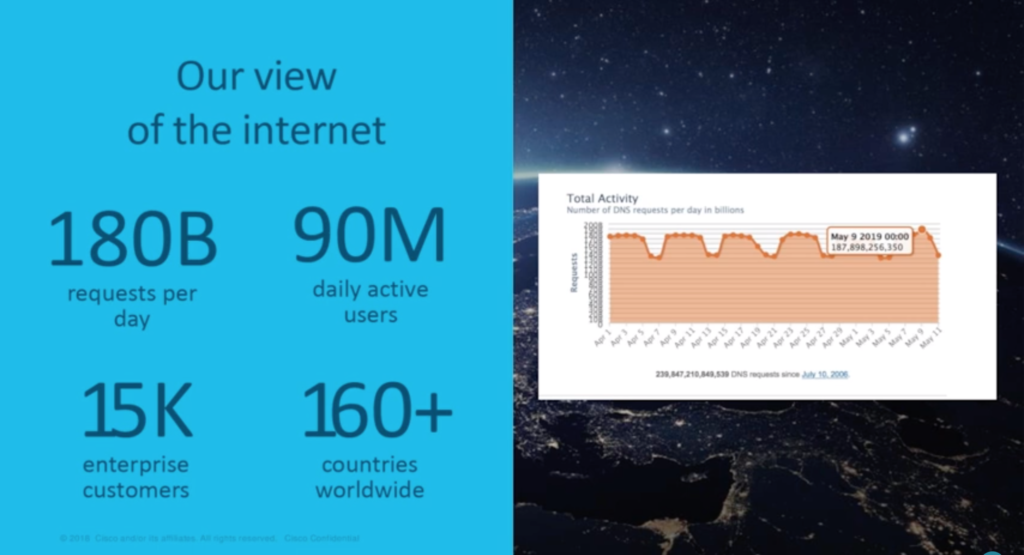
Organisations deploy Cisco Umbrella to deliver protection everywhere: boosting existing security, enabling off-network, and transforming edge security. It is based on the OpenDNS service that Cisco acquired in 2015 – a large, global DNS service with 90 million daily active users. “The vast majority of those users are people using it for free at home, for a fast, reliable internet experience,” Hugo reveals. “The 180 billion requests that we see every day give us a huge amount of data that we correlate to make decisions about where malicious activity is being hosted on the internet.” Cisco Umbrella is the enterprise-grade security solution leveraging the DNS requests to enforce security.
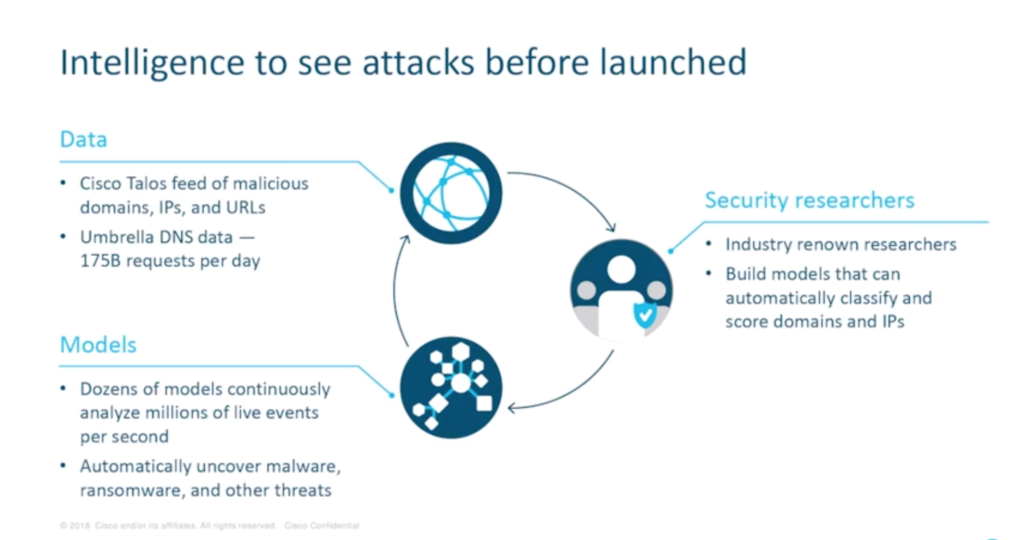
Around 20 billion threats are blocked every day by Cisco Talos, the largest, non-government threat intelligence organisation in the world. “We are up to about 300 full-time threat researchers now, analysing huge numbers of emails, of DNS requests – of every kind of connection out there – to feed into Cisco’s whole security portfolio and ensure that we are as ahead of the game as we can possibly be,” Hugo says.
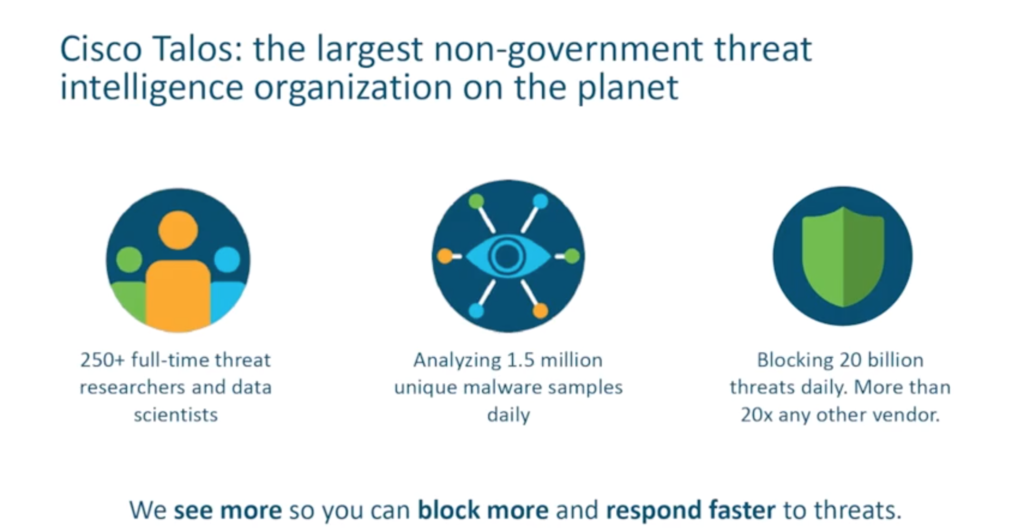
Cloud-delivered global intelligence can be used to prioritise investigations, speed up responses, stay ahead of attacks and to enrich other systems with live data.
Shadow IT is an increasing concern for many people, with the prediction that 33% of enterprise attacks will come from shadow IT by 2020. “It’s a huge business enabler in many ways, leveraging the use of these applications,” Hugo says. “But it’s getting visibility and control over exactly what your users are doing that’s becoming more and more important.”
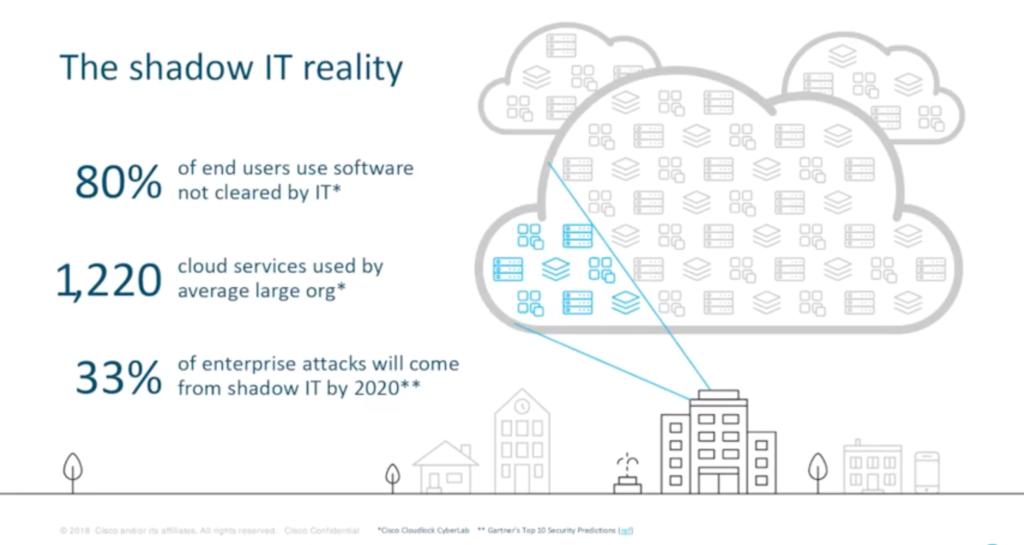
Research has shown that 80% of end users are using software not cleared by IT. Hugo reveals that many organisations do not realise how many cloud services are being used on their network. “Their expectation is they might have 30 or 40 applications running on their network, or people working from within the network, or off-network purposes. Potentially they might be aware of, or be authorising, the use of three or four collaboration apps,” he says. “The reality that we see: an average of 1,200 – often significantly more – and a vast array of collaboration apps in use.”
Hugo recommends tracking shadow IT to create a culture of “acceptance and protection” versus “detection and punishment”. Using the DNS layer, organisations can gain visibility into cloud apps and control access to them.
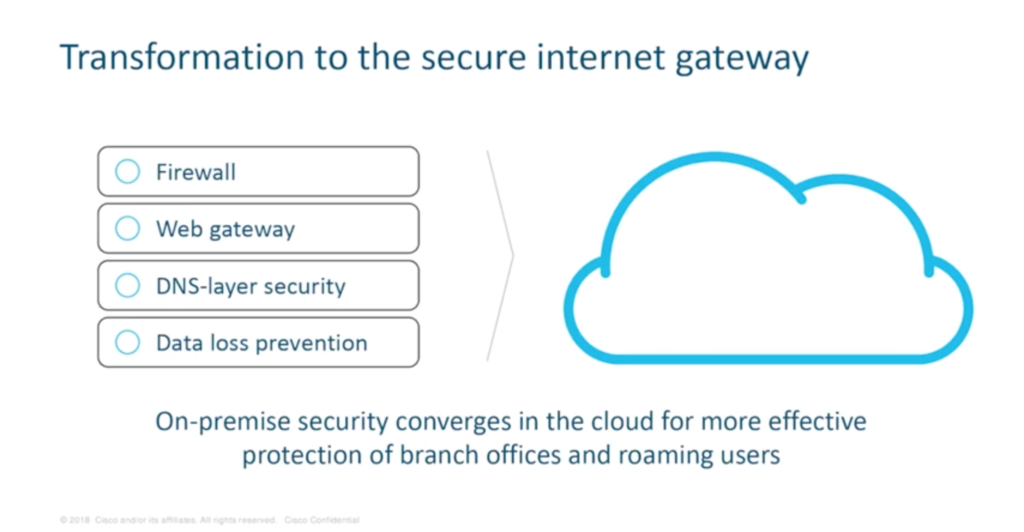
Firewalls, web gateways, DNS-layer security and data loss prevention can all be shifted to the cloud with the secure internet gateway. “We’re looking at enabling organisations to pick and choose from a suite of capabilities within a single platform,” Hugo says. “We’re looking at taking some of those traditional, appliance-based on on-premise security controls and delivering them from the cloud. You can get a pervasive layer of security to all your users and all your branches based on a single policy.”
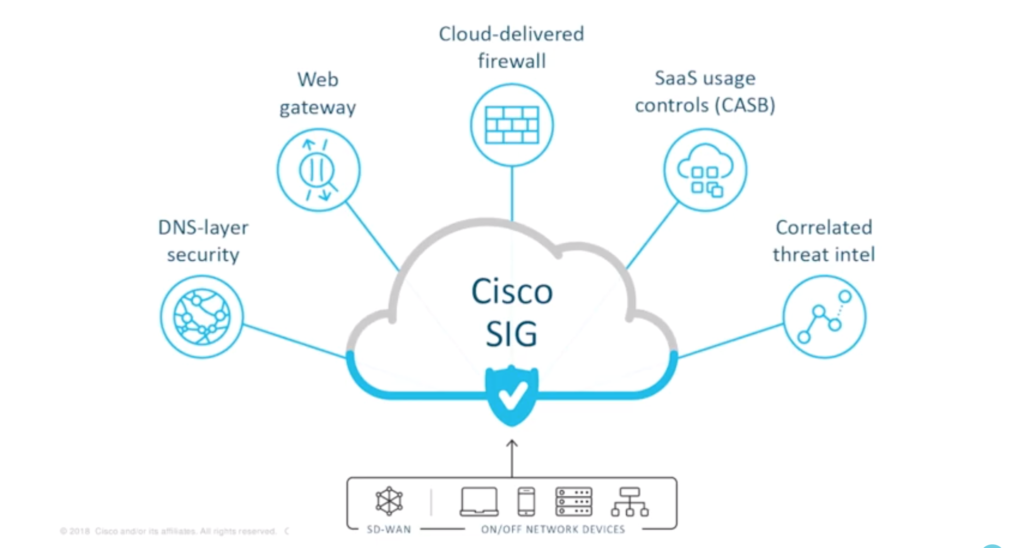
Hugo finishes his masterclass with Cisco’s vision towards secure internet gateway. “This is the way Cisco believes we need to deliver, for our customers, that choice of controls to work across the network, across application, across cloud and across all their users,” he says. “From the DNS-layer security to building out that proxy functionality where it’s needed. Cloud-delivered firewalling in the branch. Rolling in those CASB controls to leverage the proxy and to really get visibility and control over SaaS applications and to enforce DLP. And underpinning everything is the correlated threat intel.”
Check out more CISO Conferences here.
Check out Cisco Cloud Solutions here.
Watch the full masterclass of Cisco’s Hugo Bishop at the CISO Conference in May 2019







